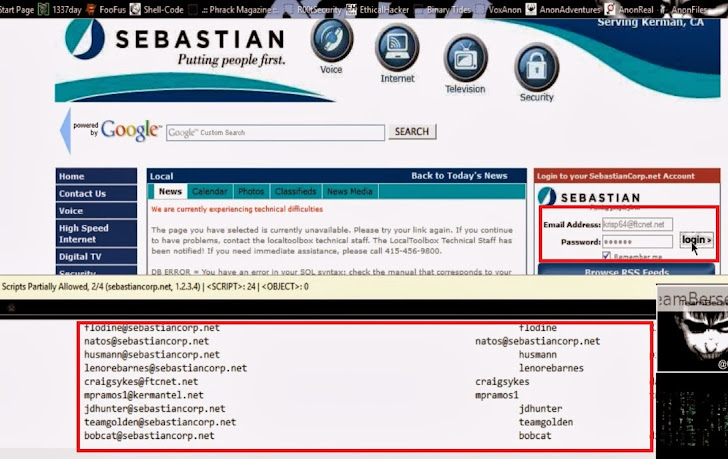
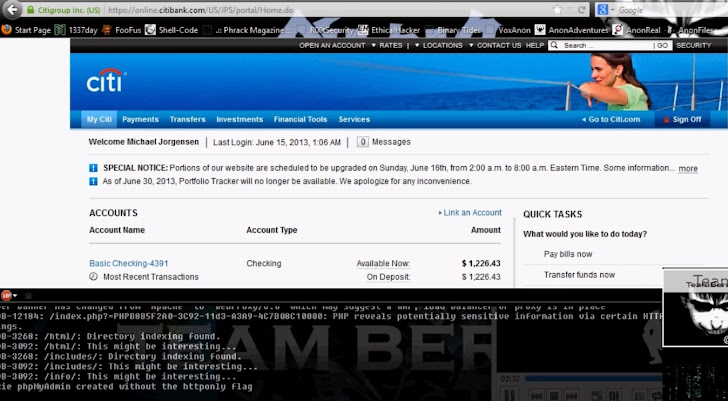
________________________________________________________
ISIS Twitter accounts:
https://twitter.com/Daash
https://twitter.com/DaashISIS
https://twitter.com/DaashConnect
https://twitter.com/DaashConnect1
https://twitter.com/DaashConnect2
https://twitter.com/DaashConnect3
https://twitter.com/DaashConnect4
https://twitter.com/DaashConnect5
https://twitter.com/DaashConnect6
https://twitter.com/DaashConnect7
https://twitter.com/DaashConnect8
https://twitter.com/DaashISIS
https://twitter.com/ISISConnect
https://twitter.com/ISISConnect2
https://twitter.com/ISISConnect3
https://twitter.com/ISIS_Connect
https://twitter.com/D3ichy1
https://twitter.com/Nour_zalam
https://twitter.com/fadou7_ilma3bar
https://twitter.com/Faysal_da3iche
https://twitter.com/sam7anA7mar
https://twitter.com/Salman7asoun
https://twitter.com/far7at_naser_3
https://twitter.com/Asad3oumran
https://twitter.com/AbouHilal_bader
https://twitter.com/Abou7amadElrasy
https://twitter.com/Dafiq_ISIS
https://twitter.com/Salman_Anwar
https://twitter.com/Jazib_moutawakil
https://twitter.com/Albakistani_JN
https://twitter.com/umar_media_ttp
https://twitter.com/Din1080
https://twitter.com/abu_elbaraa91
https://twitter.com/Din1080
https://twitter.com/ZawahiriRafidhi
https://twitter.com/interditAuPaien
https://twitter.com/Qan9Yaman
https://twitter.com/Abouyamany
https://twitter.com/AlRani1
https://twitter.com/AMouwahidin
https://twitter.com/AbouMoustapha1
https://twitter.com/Abou_illabaisse
https://twitter.com/Ja3faralsadik
https://twitter.com/E7sanALsadiq
https://twitter.com/Ja3far_aboumahdi
https://twitter.com/imam_3antar
https://twitter.com/AbuBicha
https://twitter.com/OumShaheed1
https://twitter.com/aboomusab69
https://twitter.com/riahizaid12
https://twitter.com/Khaled_nousra
https://twitter.com/MouvementSalafi
https://twitter.com/akhypotteur
https://twitter.com/Dz_Bara_ah
https://twitter.com/UmmSherazzade
https://twitter.com/Salam_nour
https://twitter.com/Abou_OmarAlchamy
https://twitter.com/Abou_jabal
https://twitter.com/Baghdadid1
https://twitter.com/Ra2if_w
https://twitter.com/Amin_3abdala
https://twitter.com/Qouyas7
https://twitter.com/zalmour_3aziz
https://twitter.com/karkhan_el_nour
https://twitter.com/Barlous_3antar
https://twitter.com/karim_soura
https://twitter.com/SrhZtn
https://twitter.com/Monimelperso
https://twitter.com/Abounizar_sadim
https://twitter.com/AbouNasir_nousra
https://twitter.com/khalid_da3ichy
https://twitter.com/Mouhran_salam_alah
https://twitter.com/Mounir3abed_nousra
https://twitter.com/MinhajNoubouwa
https://twitter.com/abou_suisse
https://twitter.com/dawlaReporter
https://twitter.com/FatimaYouYouu
https://twitter.com/Nour_Da3ich
https://twitter.com/aylan7x
https://twitter.com/Parigi6
https://twitter.com/moujahidardent
https://twitter.com/patience1900
https://twitter.com/alfuratwadijlah
https://twitter.com/CassKhattab
https://twitter.com/ibnhouss > Rachid Abou Houdeyfa
https://twitter.com/aboushaheed_
https://twitter.com/abubakr99amb
https://twitter.com/Salashh
https://twitter.com/jamilnousran
https://twitter.com/jamilnousran1
Anonymous says the following Facebook accounts are in close contact with ISIS in Syria and Iraq. They advise us to “keep a close eye” on them.
https://www.facebook.com/azizi.salina
————————————–
https://www.facebook.com/mujahiddin.bolzan
————————————–
https://www.facebook.com/sinar.cahaya.73
————————————–
https://www.facebook.com/putraijamarul77
————————————–
https://www.facebook.com/profile.php?id=100007817504822 ====> This are Junaid Hussain AkA TriCk.
————————————–
https://www.facebook.com/najmi.mie.9
————————————–
https://www.facebook.com/mohdazril.matsoom
————————————–
https://www.facebook.com/mohdrahemyl.remy
————————————–
https://www.facebook.com/safwan.wan.5661
————————————–
https://www.facebook.com/LanMazPasForAll
————————————–
https://www.facebook.com/cikgu.ihsan
————————————–
https://www.facebook.com/buxy.bux ====> (Recruiter) This woman she to brainwash young people to go to Syria to fight alongside Terrorists of the Islamic State.